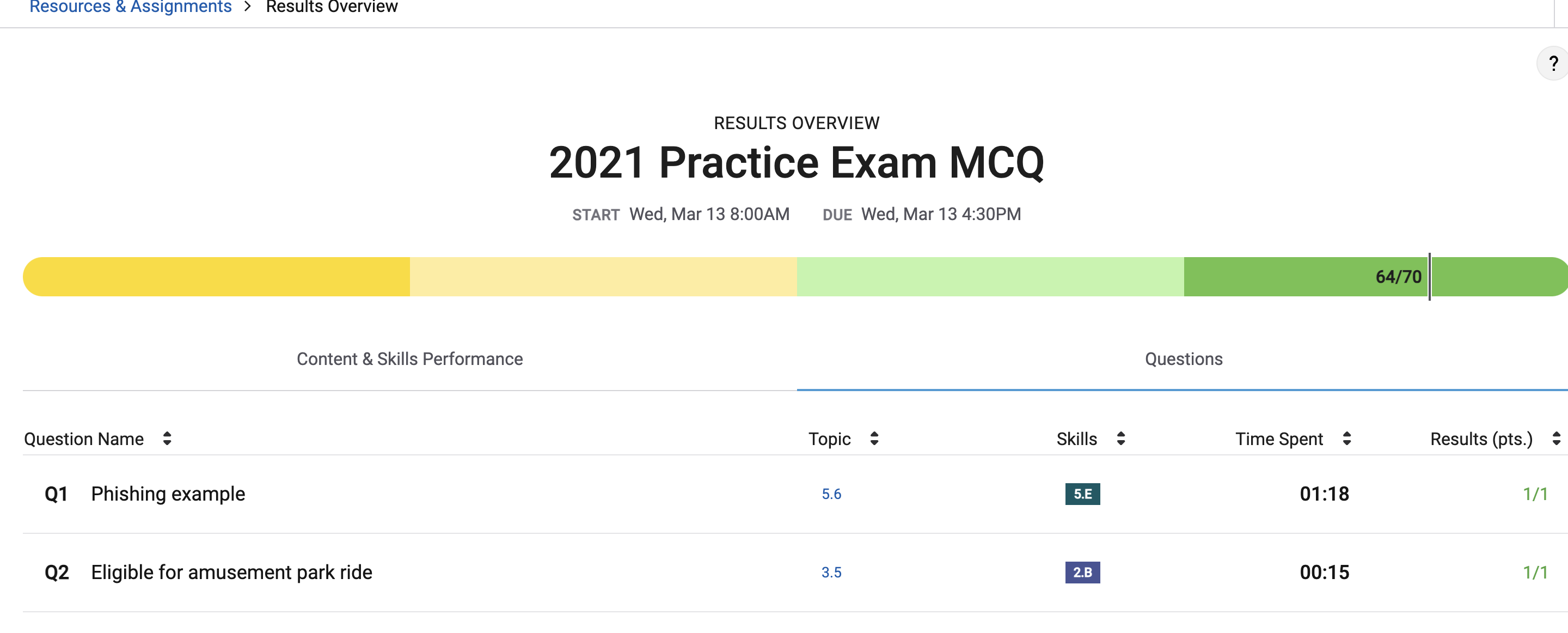
Corrections(64/70)
-
Question 16(Consequence of using Creative Commons) Question: The author of an e-book publishes the e-book using a no-rights-reserved Creative Commons license. Which of the following best explains the consequences of publishing the book with this type of license? Answer Selected: I selected Choice D(“Individuals will be legally prevented from using excerpts from the e-book in another published work.”), which is incorrect as a creative Commons license is used to allow people to use the content you have created.
Correct Answer: The correct answer is choice B(“Individuals can freely distribute or use the contents of the e-book without needing to obtain additional permissions from the author.”) as it explicitely talks about the individuals using the contents of the application from the author without consequences. -
Question 19(USE OF WEAK PASSWORDS) Question: Which of the following best explains how devices and information can be susceptible to unauthorized access if weak passwords are used? Answer Selected: I selected choice C(“Unauthorized individuals can exploit vulnerabilities in encryption algorithms to determine a user’s password from their encryption key.”) THis choice is wrong since a weak password would not effect if the encryption algorithimk and database is broken since all passwords would broken. Correct Answer: The correct answer is choice D(“Unauthorized individuals can use data mining and other techniques to guess a user’s password.”) A Weak password can just be guessed by a hacker ssince it is weak and easy and a common choice, this would cause a data leak within your account.
-
Question 23(Truth Statement About the Internet) Question:Which of the following statements about the Internet is true? Answer Selected: I selected Choice D(“The Internet uses a centralized system to determine how packets are routed.”) This is incorrect as the internet is not controlled from a central location. Correct Answer: The correct choie is B(“The Internet is designed to scale to support an increasing number of users.”) since people are able to connect to the internet and acsess it allowing increase in users.
-
Question 33(Effiency of Driving Route Algorithims) Question: A company delivers packages by truck and would like to minimize the length of the route that each driver must travel in order to reach delivery locations. The company is considering two different algorithms for determining delivery routes. Algorithm I Generate all possible routes, compute their lengths, and then select the shortest possible route. This algorithm does not run in reasonable time. Algorithm II Starting from an arbitrary delivery location, find the nearest unvisited delivery location. Continue creating the route by selecting the nearest unvisited location until all locations have been visited. This algorithm does not guarantee the shortest possible route and runs in time proportional to n^2. Answer Selected: I selected choice C(“Algorithm II provides no improvement over algorithm I because neither algorithm runs in reasonable time.”)m which is incorrect as algorithim 2 is in n^2, which is relatively proprotional and will run fast enough. Correct Answer: The correct answer is choice B(“Algorithm II uses a heuristic approach to provide an approximate solution in reasonable time.”) since it runs in n^2, which runs in enough time and is fast enough.
-
Question 55(Move element from End of list to Begining) Question: A code segment is intended to transform the list utensils so that the last element of the list is moved to the beginning of the list. For example, if utensils initially contains [“fork”, “spoon”, “tongs”, “spatula”, “whisk”], it should contain [“whisk”, “fork”, “spoon”, “tongs”, “spatula”] after executing the code segment. Which of the following code segments transforms the list as intended? Answer Selected: The answer I selected is choice A, which is incorrect since the code segment assigns the last element to the variable temp, then removes the last element of the list, then appends temp to the end of the list. THis makes it the same as the original. Correct Answer: Choice C is the correct choice since it inserts temp into the new lsit or the begining of it.
-
Question 59(Data not provided by user device) Question: RunRoutr is a fitness tracking application for smartphones that creates suggested running routes so that users can run with each other. Upon downloading the application, each user creates a username, a personal profile, and a contact list of friends who also use the application. The application uses the smartphone’s GPS unit to track a user’s location, running speed, and distance traveled. Users can use the application to review information and statistics about their previous runs. At the beginning of a run, users indicate the distance they want to run from their current location, and the application suggests a running route. Once a user accepts a suggested route, the application shares the suggested route with other compatible users in the area so that they can run together. Users are considered compatible if they are on each other’s contact lists or if they typically run at similar speeds. A basic RunRoutr account is free, but it displays advertisements that are targeted to individual users based on data collected by the application. For example, if a user’s running route begins or ends near a particular store, the application may display an advertisement for that store. Users have the ability to pay a monthly fee for a premium account, which removes advertisements from the application. Answer Selected: The answer I selected was choice A(“Adrianna’s average running speed”) which is incorrect since while Adrianna’s average running speed is useful in determining whether other users are considered compatible with Adrianna, this information is determined using data collected from Adrianna’s device. Correct Answer: The correct answer is choice C(“The current locations of other RunRoutr users”), since in order to share Adrianna’s running route with nearby users, the application needs to know the current locations of users other than Adrianna. This information is collected from other user’s devices, not Adrianna’s device.